Do you want to know what your other half is up to in instant messengers or who your child is friends with? Or may be you have been wondering whether the scammers are trying to cheat your elderly relatives? If your answer is yes, then you are now on the right page. In this post, we will tell you how to spy on other people's accounts in WhatsApp without having to physically access their phone and what you need for this.
How to Spy on a User in WhatsApp Without Having to Access His Phone
- Complex approach that requires knowledge in the field of programming and computer technology;
- Fairly simple approach that implies independent installation and configuration of software;
- Very easy approach that doesn't require additional configuration and lets you get full history of the target subscriber's activity in one click.
Here we will analyze the main ways of spying on target users of the popular messenger.
How to Spy on WhatsApp: Spoofing a MAC Address on iPhone or Android
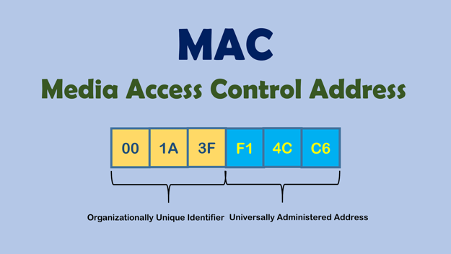
Accessing the Internet, any PC or a mobile phone transmits unique identifier assigned to it at the factory. This code of letters and numbers is called the MAC address.
The WhatsApp servers recognize the subscriber's smartphone upon receiving a response data packet from the device with its unique identifier. You can bypass it using MAC spoofing or a method that involves changing the MAC address of a device. At that, you don't have to change anything on the target subscriber's smartphone.
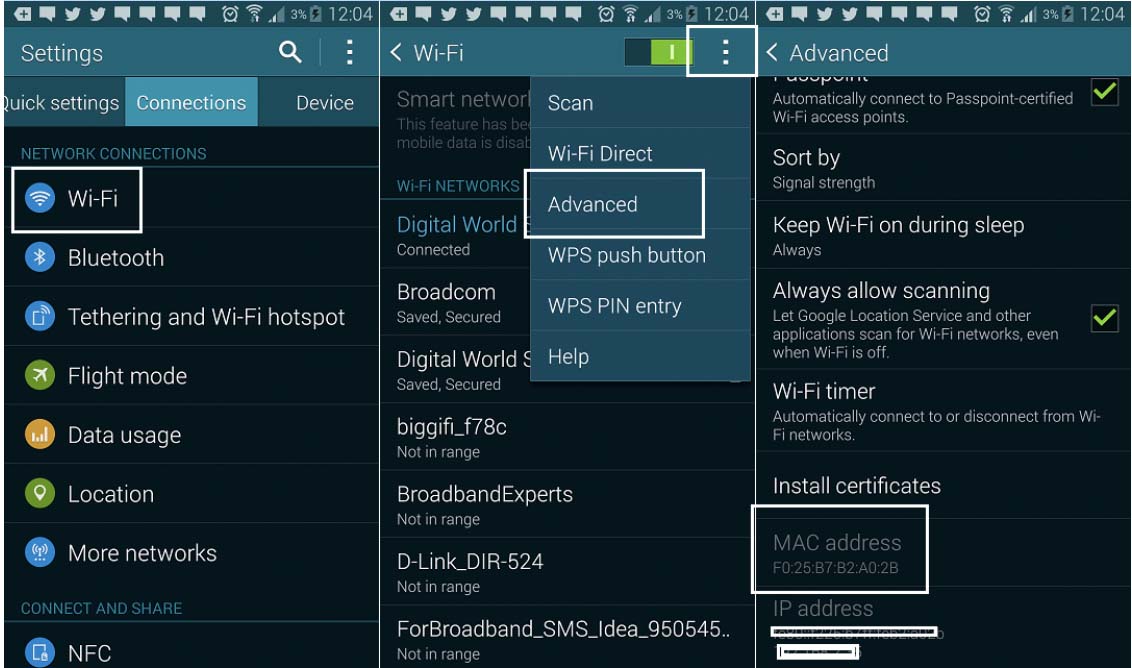
Working StagesFirst, you need to get the MAC address of the victim's smartphone. This can be done in three ways:
-
Pick up the device and go to the settings. For Android: “Settings” → “Wi-Fi Settings” → “Advanced Settings”; for iPhone: “Settings” → “General” → “About Device” → “Wi-Fi”.
- You can check the MAC addresses of the connected devices in the router settings. This approach works provided that the subscriber's phone is connected to a router you have access to, and you also know the MAC addresses of other connected devices. The latter will prevent you from mixing the identifiers up.
- You can do this via a PC or a laptop granted that (victim's smartphone and computer connected to Wi-Fi over the same network. On Windows, open "Network and Sharing Center", go to adapter settings and look at the "Status" section (the code in the "physical address" tab is the MAC address of target device); on MacOS - "System Preferences" → "Network" → "Advanced" → "Hardware".
Having learned the MAC address of your interest, you can create a spy gadget. Do it by setting up a target subscriber's account in WhatsApp on your own smartphone or by using a mobile phone that you no longer use.
- Uninstall WhatsApp messenger from your device.
- Change the MAC address of your smartphone to the device ID of the target subscriber.
- Use the applications like BusyBox or WiFiSpoof to facilitate this process.
- Install WhatsApp and specify the target phone number during registration.
- Request an activation code from the app. Be aware that it will be directed to the victim's smartphone. Therefore, the target subscriber's phone should be in your hands at this time so that you can quickly read the message and delete it.
- Change the MAC address on your smartphone to the original one.
If you managed to do things correctly, your phone will store the full correspondence, call history as well as sent and received media files from the WhatsApp target account. Remember that having changed the MAC address again, you won't receive new messages of the target user.
Using the WhatsApp Web Version for Spying on the Users
In 2015, WhatsApp developers presented the computer version of application. However, despite of its convenience, such a version provided additional opportunities for spying on other people.
Now, physically accessing the target user's phone for 1 to 2 minutes and using the web version of WhatsApp, people can easily read all the user correspondence and check his call log and contact list.
How to Do This?- Go to the WhatsApp website.
- Open the messenger on a user's device.
- Select "WhatsApp Web" in settings and scan the QR code.
Exploiting this approach, you can easily spy on messenger's user provided the person of your interest keeps using it on their Android or iPhone.
When monitoring activity in this way, remember that the web version is synchronized only provided the instant messenger runs smoothly on the phone. Reinstalling WhatsApp or making some ther changes in the software, you will have to re-scan the QR code.
Also, do not forget that the target user may accidentally learn that he is being spied on:
- After recent update, smartphones display notifications of new sign-in from another device.
- Active connections to WhatsApp Web are displayed in the messenger settings.
To avoid exposure, we recommend that you view the target user activity once, and then log out of his account on your computer.
Spying on WhatsApp Without Accessing Target Phone
Unfortunately, the abovementioned methods not only require some knowledge and skills from the hacker, but also require quick physcial access to the victim's phone. If this is impossible or you have absolutely no wish to configure software settings, we recommend that you use the third-party applications that allow you to effortlessly spy on WhatsApp on both Android and iPhone.
One of the popular solutions is WhaTracker software installed on a remote server and ready to use. Interacting with the software via web interface, you can launch the application from any device such as PC, laptop, smartphone or tablet running one of the modern operating systems like iOS, Android, Windows, or MacOS. In this case, you will only need to specify the target phone number in the international format. Here you can learn how it works.
The Final Word
You can choose the most suitable way of spying on WhatsApp users of your interest. However, you should remember that most effective methods involve direct interaction with the victim's phone. It is possible if the person of your interest is your child or other half. But when it comes to your friends or colleagues, this option is unlikely to be appropriate. In most cases, we recommend that you use the third-party applications to fully eliminate risks of being caught and instantly hack the target account.